Related Solutions
Related Product Series
Related Product
From the May 2021 issue of Security Business Magazine:
-----
Motion detectors have long been key tools in a security designer’s toolbox; however, they are also often the subject of nuisance alarms and installer frustration. They are purpose-built devices with a single-purpose application, and they usually perform well. That said, while the technology has certainly evolved over the years, it has not necessarily kept pace with the advancements that have been made in video surveillance or access control, for example.
At least one firm is looking to spur this evolution more quickly, with a goal of reinventing the motion detector as a smarter device with broader applications – elevating its position to an edge device with connectivity, programmability, and intelligence.
Motion Detectors: Then and Now
The first motion sensor was invented in the 1940s by Samuel Bagno using technology that was developed during World War II. Using his military knowledge of radar, Bagno developed a device that used ultrasonic waves and the Doppler effect to detect motion in a room. By the 1970s, these motion detectors were popular components in home burglar alarm systems; however, their technology made them prone to false alarms, as the ultrasonic waves could easily be disrupted by innocent disruptors such as wind or a clock chime.
In the 1980s, advancements in technology brought us the infrared motion sensor. Active infrared sensors work by emitting infrared radiation, detecting differences in temperature between an object and its surroundings. Passive versions of these detectors have no emitters; instead, they use sensors to detect the difference in infrared emitted by objects in range. Microwave detectors operate on the same principle of the original ultrasonic devices – microwave pulses are sent out and the device measures the reflections back, looking for changes.
Many motion detectors use multiple technologies in one in an effort to reduce false alarms. Passive infrared, for example, is commonly paired with microwave detection. Both sensors would need to be activated before an alarm is triggered.
The Next Step: LiDAR
Fast forward to today, and companies at the forefront of motion detection have been implementing a new technology: Light Detection and Ranging (LiDAR). Popularized by the autonomous vehicle industry and smartphone manufacturers, LiDAR uses a pulsed laser to calculate the distance from the laser source to an object. By measuring the light from the laser’s reflection, 3-D representations of surfaces can be created. Once a static scene is established, changes to that scene can trigger a motion alarm.
The advantage of LiDAR in this application is how finely the detection area and target object size can be tuned, and how well a target can be tracked. By adding intelligence to how these values are programmed, the days of the security technician “walk test” to determine the detection area may be numbered.
I sat down with the Director of Marketing for Optex, a company known for its motion detector technology – the newest of which uses LiDAR. “Optex LiDAR sensors enhance motion sensor capabilities by providing more detection customization and on-board laser analytics that give you the ability minimize false and nuisance alarms,” he says. “We also have the ability to accurately provide the exact size, speed and location of an object and transmit that data to multiple platforms.”
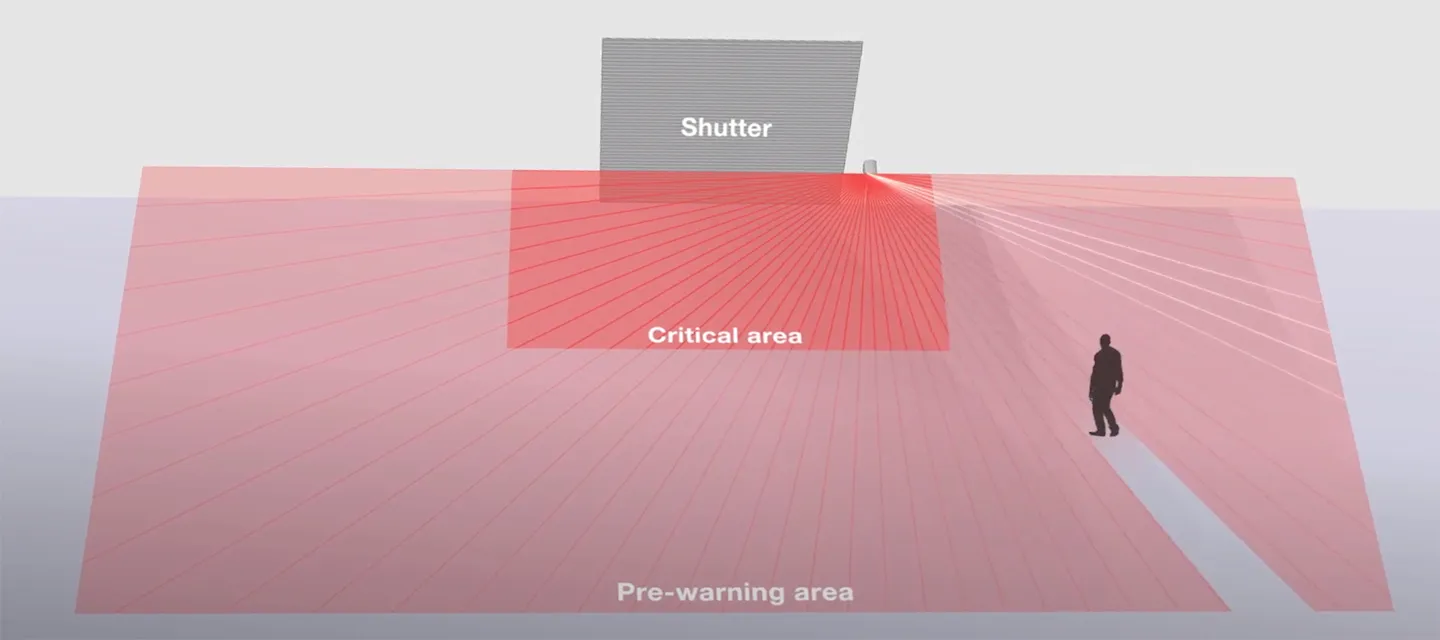
LiDAR-based motion sensors from Optex feature rectangular detection areas, which simplifies design and implementation.
The company has implemented additional features that make these LiDAR-based detectors indistinguishable from the long-standing industry staple. An integrated camera can help installers determine the exact field of view and area of detection. The LiDAR sensors themselves have rectangular detection areas, which drastically simplifies design and implementation over traditional fan-shaped detection areas. This enables coverage of large areas with fewer sensors, since they can be placed in locations that eliminate overlap. Rectangular detection areas can be easily used to create detection “planes” along a perimeter, building face or rooftop, for example.
Intelligence Reduces False Alarms
The amount of intelligence built into the device had me wondering whether these motion detectors have jumped categories and are in competition with motion analytics-equipped video surveillance cameras. Marco says the motion detectors outperform video analytics because they are purpose-built for the application and have detection technology superior to video cameras. “The major value-add for using a sensor with a motion detection analytic is to create what we call an IP video double knock,” Marco explains. “Since sensors do not rely on light as a source for detection, we are not affected by the various causes of video-based false/nuisance alarms.”
In fact, motion detectors work best when used in tandem with video surveillance. “We can work together with video analytics to trigger an event when both forms of detection are confirmed,” Marco says. “When an event gets triggered by video analytics but not the sensor, you hold the alarm and vice versa. This is how we work with major video platforms by identifying/recognizing hardware on a platform and grouping them together to create unique security event rules.”
Optex motion sensors can transmit coordinate data to integrated video management platforms to help direct cameras to track a target. Because visible light is not a requirement, they can help track targets in darkness, in conditions when a video surveillance camera may be challenged. If a video camera is not present to help validate the motion detector alarm, the device itself can store a snapshot of the alarm-inducing condition for retrieval by a security operator.
With motion detectors joining the ever-growing Internet of Things (IoT), ensuring the devices have the appropriate level of cyber features must be considered. “We realize security threats to our end-users are not only from an intrusion point of view, and Optex has developed up-to-date cybersecurity features,” Marco says. “We work closely with our end users, channel and technology partners to help meet cybersecurity specifications.”
-----
You may be interested in


Protecting Medical Marijuana Facilities with OPTEX REDSCAN Advanced LiDAR Detection
Medical marijuana greenhouses and production sites are high-value targets requiring protection that goes beyond traditional surveillance. Intrusion detection must be accurate, intelligent, and adaptable to both indoor and outdoor environments.
































